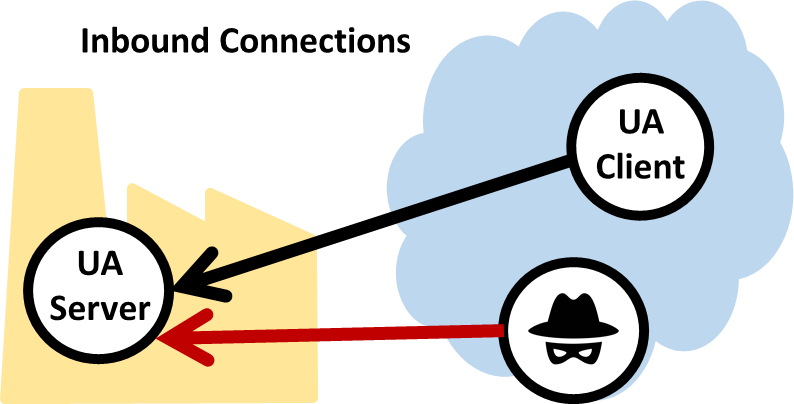
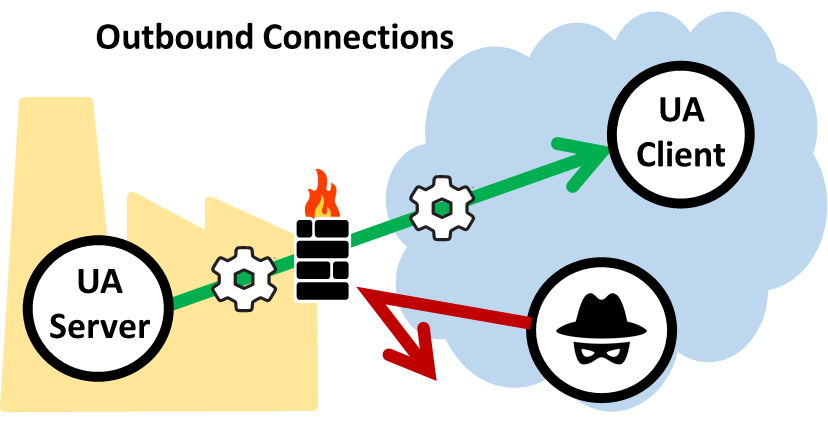
Considering Prefab
An uncle of mine was an entrepreneur and quite a do-it-yourselfer. His main businesses included a restaurant and a propane gas distributorship, but he was a real hands-on kind of guy, and spent a few summers building a cottage on Seneca Lake in Upstate New York. It was an ongoing project, always in a state of “finishing.”
The first stage, a small one-story, was mostly done, with panelled living room and functional kitchen, although some of the bedrooms in the back were unfinished—partially drywalled with exposed plumbing and electrical. The next stage was planned as a large two-car garage to be capped by a second story master bedroom and office with large glass doors and picture windows overlooking the lake.
That was the plan, anyway. The reality was that his various businesses and other interests intervened. For the several summers that my brother and I worked with and for him, the garage was his workshop, while progress on the second story proceeded in fits and starts. A year or two after I’d moved away from the area, it was a heartbreak to find out that the cottage had caught fire and burned to the ground, due to a short-circuit in the wiring. Nothing useful was left but the original concrete slab.
I never got to see that cottage completed. But my uncle was not deterred. He rebuilt, prefab. In a few weeks he had a very nice two-story cottage, with a two car garage and great views of the lake from picture windows on both stories. Rather than wasting his time framing rooms, running wiring, joining pipes and hanging sheetrock, he was out on the water sailing, or cooking up a barbeque with his cousins and family.
The lesson for me? Sure, maybe you can do it all yourself. But should you? It could take more time than you expect, and the results may not be what you were hoping for. Sometimes it’s best to leave the tedious, difficult, and specialized work to the experts, and focus on what brings the most value, or the most fun.
As we explained in a recent article published in Automation.com, this is the principle behind working with Skkynet’s ETK, and its OPC UA framework, rather than a software development kit (SDK). Using an SDK can take an expert programmer 12 to 18 months to build an OPC UA server. Meanwhile, a developer who uses the ETK gets a pre-built OPC UA server, and can focus on his or her applications.
Some people, like my uncle, seem to enjoy doing it themselves. They rise to the challenge, and given enough time they can succeed. And then there’s the prefab option: buy, install, and run. The grunt work is done. Drop your hammer and rig the sailboat. That’s the benefit of the ETK’s OPC UA framework—the difficult and boring work is done, so the developer can focus on what he or she knows and does best.