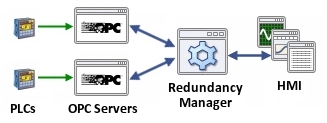
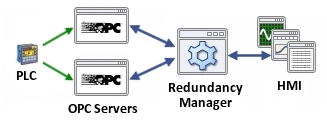
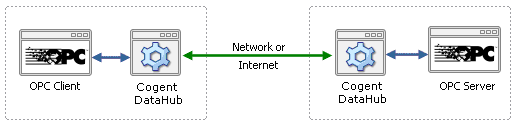
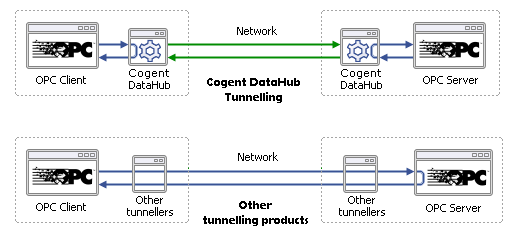
What is a Good Approach to Industrial SaaS?
“A chain is only as strong as its weakest link,” goes the old saying. How true that is in industrial control systems. One small glitch on an assembly line can force a shutdown. Lack of a single ingredient in a chemical plant or food processing system might wreak havoc. Factory automation, power generation, resource extraction and processing, transportation and logistics are all supported by chains of mechanisms, hardware, and software, as well as operators and engineers that must each carry out their mission to produce the expected output, product, or service.
From time to time, new technologies come along that provide cost savings, better performance, and ease of use—new links for the chain. Electrical relays, pneumatic controls, DCSs, PLCs, RTUs, SCADA, plant networks, and fieldbus were all at one time proposals on the drawing board. Each had its evangelists and skeptics, and each was thoroughly tested. Once its value was proven, each one has become a strong link in the automation chain.
One of the latest technologies to be proposed is software as a service (SaaS). SaaS provides access to hosted software over a network, typically the Internet, and is closely related to the concepts of smart factories, cloud computing, industrial Internet, machine-to-machine (M2M), and the Internet of Things (IoT). Adding SaaS to an industrial process control system means adding data collection, integration, and/or distribution capabilities beyond the limits of most existing in-house systems.
SaaS can open wider access to plant data in real time, which can support real-time monitoring of processes, supply the big data needed to drive predictive maintenance programs, provide the ability to outsource customer care facilities, deliver real-time KPIs, and otherwise leverage the value of new or existing SCADA investments. Implemented well, software as a service should also provide a significant cost savings over the traditional avenue of software ownership.
To be truly useful, though, industrial software as a service should be secure, quick, and robust, as well as adaptable and convenient to use.
Secure
Industrial systems require the highest possible level of security. “IT security was the most oft-cited obstacle to setting up smart factories,” according to Lopez Research in their January 2014 article Building Smarter Manufacturing With The Internet of Things (IoT). A comprehensive report from GE titled Industrial Internet: Pushing the Boundaries of Minds and Machines states, “The Industrial Internet will require putting in place a set of key enablers and catalysts,” including, “a robust cyber security system and approaches to manage vulnerabilities and protect sensitive information and intellectual property.” Achieving this level of security requires a comprehensive approach, including secure servers, authorization and authentication of users, encrypted data transport mechanisms, and keeping all firewall ports closed at the plant level.
Quick and Robust
Industrial software as a service should provide as close to real-time performance as the network or Internet infrastructure will support. This means that data updates should be in milliseconds, not seconds or minutes. It should be able to handle thousands of data changes per second, and support redundant connections with hot swap over capability.
Adaptable
Industrial systems are diverse, built from a wide range of equipment and controls, using various data protocols, and come in all sizes. Industrial SaaS should be able to connect seamlessly to any new or installed system at any number of locations with no changes to hardware or software. It should use open data protocols and APIs. Ideally it should work with any size of system, from complete DCS and SCADA systems down to a single machine or embedded device. Running as a cloud-based service, it should also readily scale up or down depending on user needs.
Convenient
To gain acceptance in the market, industrial SaaS should be convenient to use. It should be easy to demo, sign up for a service plan, configure connections, and monitor usage and costs. It should offer off-the-shelf tools to get your data to and from the cloud with no programming, provide the ability to easily integrate data from multiple sources, and include options like data storage and HMI displays–all without disrupting the industrial process in any way.
Redesigning for Security
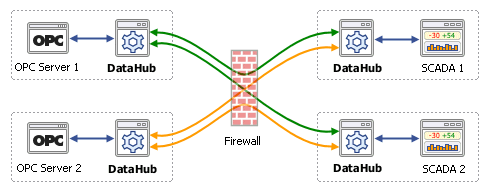
Among these requirements, the most challenging is security. Without the ability to fully protect mission-critical processes and their data, industrial SaaS is simply a non-starter. And yet, a fundamental characteristic of virtually all industrial systems presents a significant security risk for any cloud-based system: a firewall port must be kept open.
The current approach to this problem is to implement VPN (virtual private network) technology. A VPN creates a secure space on a network that is isolated from all other traffic. However, this is not an ideal solution because a VPN allows every connected device and user full access to every other device and user. For a single control room, this may not seem to be too much of an issue. But in the world of cloud computing, operators and field engineers will expect to have access to data on tablets and cell phones, which can easily fall into the wrong hands.
Ironically, using a VPN might even turn a plus into a minus. A strong selling point of SaaS is its potential to act as a platform for sharing limited data sets with authorized suppliers, customers, and other parties. Few IT departments would be willing to hand over the keys to the store by providing these players with access to the corporate VPN.
A better approach is needed. Although VPN might be useful under certain circumstances, it doesn’t address the fundamental design issue of virtually all industrial data communication, which is the client-to-server architecture. To get data out of an industrial system, a client needs to request it from a server. So, if any kind of cloud service needs access to process data from a server located behind a plant firewall, a port on that firewall must be kept open at all times. And open firewall ports are inherent security risks.
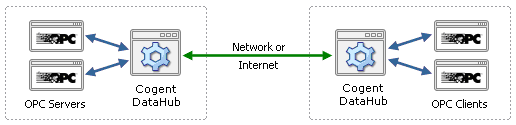
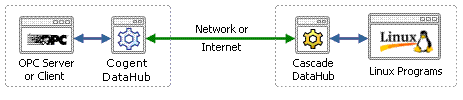
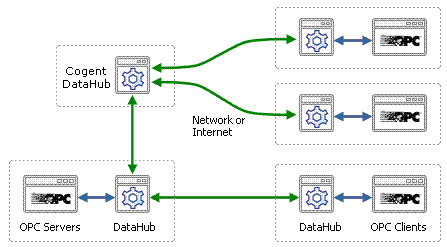
What is required is a new design. SaaS transmits data over the Internet, and there is a TCP protocol that supports a different connection model: WebSocket. With the right kind of engineering this protocol can be applied to industrial data communications in a way that allows only out-bound connections from the plant to the cloud. No in-bound connections are necessary; no plant firewall ports need to be left open. Once the connection is established, the data can flow in both directions. Or you can choose to make all or some of your data read-only, preventing any write back from the cloud. Whichever approach you take, the data flows through a closed firewall, making your plant effectively invisible to Internet attacks.
In addition to protecting the plant, with this design no primary or mission-critical control need be performed by the service. All local control can remain untouched. The system manager has complete flexibility over what data gets passed to the service, and the connection can be configured as read-only if desired.
Real-Time Data
Next to security, a good industrial SaaS solution should perform well. When you mention anything related to cloud computing, most people conjure up an image of a giant database sitting up in the air somewhere in which you store data, and pull it out when you need it, like Gmail or Dropbox. Although that model works fine for storing static data, industrial systems function in real time. The true value of industrial SaaS should be realized through real-time performance, which requires a fundamentally different architecture on the cloud.
One good approach is for the service provider to host a real-time, memory-resident database that can receive and retransmit data at speeds of tens of thousands of data changes per second. Achieving these speeds is possible through a publish/subscribe method of data delivery, an event-driven model in which a client registers for data changes one time and then receives subsequent updates immediately after they occur. This kind of low-latency system adds almost nothing to the overall data transmission time, effectively keeping throughput speeds to just a few milliseconds more than network propagation time.
To further speed up throughput, all data should be handled in the simplest possible format, by taking a data-centric approach. This kind of system is able to work with all kinds of data sources and users, such as control systems, OPC servers, databases, spreadsheets, web pages, and embedded devices. When a data source connects, its data gets stripped of all unnecessary formatting (XML, HTML, OPC, SQL, etc.) and is added to a universal data set comprising data from all connected sources. Updates to any point in this data set are immediately passed to any client registered for them. At the receiving end the data can be transformed back into its original format, or into whatever other format the client might need.
Making it Work
Anyone who has spent any time in industrial automation soon discovers that every system is unique. Different industries, plants, and project requirements demand a wide range of tools, machines, and other devices which are provided by hundreds of independent suppliers, and installed by a multitude of diverse system integrators and plant engineers worldwide.
Good industrial SaaS should fit as many of these different types of systems, protocols, and brands of equipment as possible. It should use open, standard protocols like OPC, TCP, and ODBC. If it is completely vendor agnostic, it is in the best position to leverage investments in existing equipment or enhance new installations with real-time data connectivity. Ideally it should be capable of being added to a SCADA system, function as an HMI for an individual machine, or access RTUs and even individual embedded devices.
As a cloud-based system, we would expect the service to be able to scale up or down to meet the needs of its users. This means the ability to handle bursts of high-speed activity in the data flow at any given moment, as well as the capacity for quick reconfiguration to support expansion requirements of a growing system. Users should be able to add data points to a particular device, or bring on new devices, new SCADA systems, even new locations and installations through an easy-to-use interface.
Finally, data from the service should be readily available to key decision-makers in the way they can best use it, be it an operator using an HMI for monitoring and supervisory control, a field engineer picking up the latest figures from the home plant, an analyst running real-time scenarios from facilities spread across three continents, a just-in-time supplier whose system is keyed to current production levels, or a plant manager responsible for production at a group of isolated facilities. Good industrial software as a service should be a solid link in the chain, reducing costs, meeting the needs of all players, and doing it securely, quickly, and conveniently.