Recent IoT Attack on Dyn Calls for Secure By Design
The recent denial of service attack on Dyn, a DNS service company for a huge chunk of the Internet, sure woke up a lot of people. Somehow when it happens to you, you tend to feel it more. Twitter, Netflix, Reddit, eBay, and Paypal users certainly felt it when they couldn’t access those sites. Now that most of us are awake, what can we do about it?
In the short term, not a lot, apparently. In a recent article about the attack titled Vulnerability Is the Internet’s Original Sin, Internet security expert and author of Dark Territory: The Secret History of Cyber War, Fred Kaplan points out that from the beginning the costs and challenges of designing security into the Internet from the ground up was considered too challenging and costly.
Kaplan tells how, back in 1967, Willis Ware, the head of the Rand Corporation’s computer science department and a NSA scientific advisory board member, wrote a paper warning the ARPANET team and others that “once you put information on a network—once you make it accessible online from multiple, unsecure locations—you create inherent vulnerabilities … You won’t be able to keep secrets anymore.”
The Dyn attack was simple in concept and easy to execute. The devices used were accessible household appliances and electronics, configured out of the box with simple default user names and passwords like “username”, “password”, and “12345”. The virus cycled through these default credentials to recruit thousands of devices into a giant collective, which was then coordinated to flood Dyn with traffic.
To prevent this kind of hack, device manufacturers may start updating their devices to ensure more secure usernames and passwords. But that ignores the elephant in the room. The fundamental problem is that these IoT devices are available (they are always on, ready to communicate over the internet), they are accessible (they can be seen on the internet), and they are numerous (with numbers growing exponentially). This combination of availability and accessibility, multiplied by the huge numbers, makes IoT devices perfect for coordinated attacks. We can be sure that the bad actors are already working hard on defeating username/password protection on IoT devices.
Considering the first of these three critical factors, IoT functionality requires that IoT devices are available for communication. There is not a lot we can do about availability. Secondly, the business opportunities and economic promise make device proliferation unstoppable. We have to expect continued rapid growth. But we can do something about the third critical factor: accessibility.
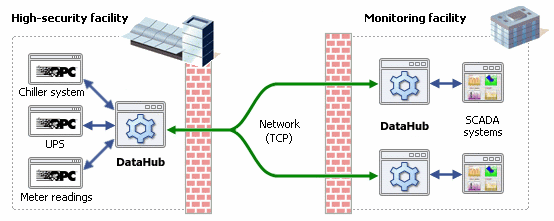
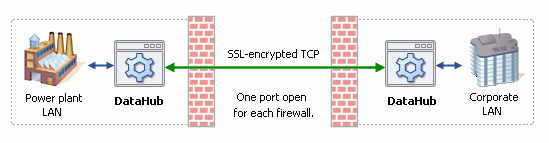
No IoT device should be sitting on the Internet with one or more open ports, waiting for something to connect to it. The device can and should be invisible to incoming probes and requests to connect. A hacker or bot should not even see the device, let alone be given the chance to try a username or password. That technology exists, is easy and inexpensive to implement, and has been proven in thousands of industrial installations for over a decade. Governments and manufacturers need to be employing it across the full range of IoT applications.